Are you entranced by the revolutionary potential of blockchain but perplexed by the security risks that come with it? Welcome to the ultimate guide that demystifies blockchain security, a cornerstone topic that can make or break your experience in the crypto world. Whether you’re a seasoned blockchain developer, an avid cryptocurrency trader, or a curious newcomer, this comprehensive blog post will equip you with everything you need to know to navigate this complex landscape safely.

Why Blockchain Security Matters
In a world where data breaches and cyber-attacks are increasingly commonplace, the security of blockchain technology stands as a critical concern. As blockchain continues to gain traction in various sectors—from finance to supply chain management—understanding its security mechanisms isn’t just an option; it’s a necessity. A single vulnerability can jeopardize millions of dollars and tarnish the reputation of businesses and individuals alike. That’s why diving deep into the intricacies of blockchain security can empower you to make informed, secure decisions in your blockchain endeavors.
Quick Takes
| Section Heading | Key Takeaways |
| Why Blockchain Security Matters | Understanding the critical role of security in safeguarding blockchain’s credibility and utility. |
| What is Blockchain? | Basic introduction to the concept and structure of blockchain technology. |
| How Does Blockchain Work? | Overview of the technical mechanics behind blockchain. |
| Historical Security Breaches | Learning from notable security incidents in the blockchain space. |
| Trends in Blockchain Security | Insights into evolving threats and defenses, supported by current data. |
| Cryptography in Blockchain | The essential role of cryptography in securing transactions and data. |
| Consensus Algorithms | How consensus mechanisms like Proof of Work (PoW) and Proof of Stake (PoS) impact security. |
| Smart Contracts | Examining the vulnerabilities and security aspects of smart contracts. |
| 51% Attacks | Understanding the risks and implications of a 51% attack. |
| Double Spending | Explanation of what double spending is and how blockchain minimizes this risk. |
| Phishing Scams | Common types of phishing scams in the blockchain space and how to avoid them. |
| Exchange Vulnerabilities | Identifying security loopholes in cryptocurrency exchanges and how to protect oneself. |
| Sybil Attacks | Advanced discussion on the risks of Sybil attacks and mitigation strategies. |
| Routing Attacks | How routing attacks compromise blockchain networks and ways to defend against them. |
| Eclipse Attacks | Understanding eclipse attacks and how they can be mitigated. |
| Multi-Signature Wallets | Utilizing multi-signature wallets for enhanced security. |
| Cold Storage | The pros and cons of using cold storage for cryptocurrency. |
| Hardware Wallets | A comprehensive guide to choosing and using hardware wallets. |
| Current Laws and Regulations | Overview of existing regulations affecting blockchain and crypto security. |
| Quantum Computing Threats | Discussing the potential future risks posed by quantum computing to blockchain security. |
| Future of Blockchain Security | Predictions and insights into the evolving landscape of blockchain security. |
Understanding Blockchain
Blockchain technology serves as the backbone for a plethora of applications, including cryptocurrencies like Bitcoin and Ethereum. Understanding its basic structure and how it operates is crucial for grasping the intricacies of blockchain security.
What is Blockchain?
A blockchain is a distributed, immutable ledger that records transactions across multiple computers. Each transaction is grouped into a block, and these blocks are chained together in chronological order. This design makes it difficult to alter past transactions, thereby enhancing the security and integrity of the data.

How Does Blockchain Work?
The blockchain network consists of nodes, each containing a copy of the blockchain. When a new transaction is initiated, it is broadcast to all nodes in the network. Nodes then validate the transaction through a consensus mechanism before adding it to their respective copies of the blockchain.
Consensus Mechanisms
Consensus algorithms like Proof of Work (PoW) and Proof of Stake (PoS) play a critical role in validating transactions. PoW requires nodes to solve complex mathematical puzzles, while PoS relies on the stake or ownership of tokens to choose the validating node.
| Consensus Algorithm | Features | Pros | Cons |
|---|---|---|---|
| Proof of Work (PoW) | Miners solve complex mathematical problems to validate transactions and create new blocks. | Highly secure, Decentralized | Energy-intensive, Risk of centralization |
| Proof of Stake (PoS) | Validators are chosen to create new blocks based on the number of coins they hold and are willing to “stake” as collateral. | Energy-efficient, Reduced risk of centralization | Risk of “nothing at stake”, Lower decentralization |
| Delegated Proof of Stake (DPoS) | A voting system where a fixed number of elected delegates validate transactions and create new blocks. | Fast transactions, Low fees | Risk of centralization, Less secure |
| Practical Byzantine Fault Tolerance (PBFT) | A state machine replication algorithm designed to work efficiently in asynchronous environments. | Highly efficient, Suitable for private blockchains | Not suitable for public blockchains, Complex implementation |
Immutability and Transparency
Once a block is added to the chain, it becomes immutable, meaning it cannot be altered or deleted. This immutability, combined with the transparency of the distributed ledger, adds layers of security and trust to the blockchain network.
Smart Contracts
Smart contracts are self-executing contracts with the terms directly written into code. They operate on the blockchain and automatically execute actions when predetermined conditions are met.
Why Blockchain Security is Integral
Blockchain’s design inherently includes various security features like cryptography and consensus mechanisms. However, as the technology evolves and finds broader applications, the security landscape must adapt to new threats and challenges.
The Evolution of Blockchain Security
As blockchain technology has matured over the years, its security landscape has undergone significant changes. From the initial days of Bitcoin to the rise of smart contracts and decentralized finance, the need for robust blockchain security has never been more critical. This section delves into the historical perspective, current trends, and the future outlook of blockchain security.
Historical Security Breaches
Understanding the past is crucial for securing the future. Blockchain technology has not been without its share of security incidents, ranging from exchange hacks to smart contract vulnerabilities.
Notable Incidents
- The Mt. Gox Hack: One of the earliest and most infamous breaches, where approximately 850,000 Bitcoins were stolen.
- The DAO Hack: A vulnerability in a smart contract led to the theft of around $50 million in Ethereum.
Trends in Blockchain Security
As blockchain technology evolves, so do the threats it faces. However, advancements in cryptography, consensus algorithms, and multi-layer security protocols have contributed to a more secure environment.
Data-Driven Insights
Blockchain security trends can be gleaned from numerous reports and studies that analyze vulnerabilities, attacks, and emerging threats.
Emerging Technologies
Technologies like zero-knowledge proofs, sharding, and layer 2 solutions are shaping the future of blockchain security. These technologies aim to solve existing issues like scalability while enhancing security.
Future Outlook on Security Measures
As blockchain finds applications beyond cryptocurrency, such as in smart contracts and the rise of DeFi, security measures must also evolve. Upcoming security trends involve machine learning for anomaly detection, real-time audits, and automated threat hunting.
Key Elements of Blockchain Security
Blockchain technology is often touted for its robust security features. While it’s true that blockchain offers several layers of protection against fraud and unauthorized activities, understanding these key elements is crucial for anyone involved in the blockchain ecosystem, from developers to end-users. In this section, we will examine the cornerstone elements that contribute to blockchain security.
Cryptography in Blockchain
Cryptography is the bedrock of blockchain security. It involves the use of mathematical algorithms to secure transactions and control the creation of new units.
Hash Functions
Hash functions take an input and produce a fixed-length string, which appears random. The same input will always produce the same output, but even a minor change in input will produce such a drastic change in output that the new hash will appear uncorrelated with the old hash.
Digital Signatures
Digital signatures provide a layer of authenticity, ensuring that the message or document has been signed by the private key of the purported sender.
Consensus Algorithms
Consensus algorithms are protocols that consider a transaction as legitimate and add them to the block. Different algorithms exist for this purpose, such as Proof of Work (PoW) and Proof of Stake (PoS).
Proof of Work
In a PoW system, network participants compete to solve a mathematical problem, and the first one to solve it gets to add the new block.
Proof of Stake
In PoS, the creator of a new block is chosen in a deterministic way, depending on its wealth, also defined as a stake.
Smart Contracts
Smart contracts are self-executing contracts where the terms are directly written into lines of code. These are particularly popular in decentralized applications (dApps) and need to be securely written to prevent vulnerabilities.
Security in Smart Contracts
The security in smart contracts is of paramount importance as they execute automatically. Any loophole could be exploited, leading to the loss of valuable assets.
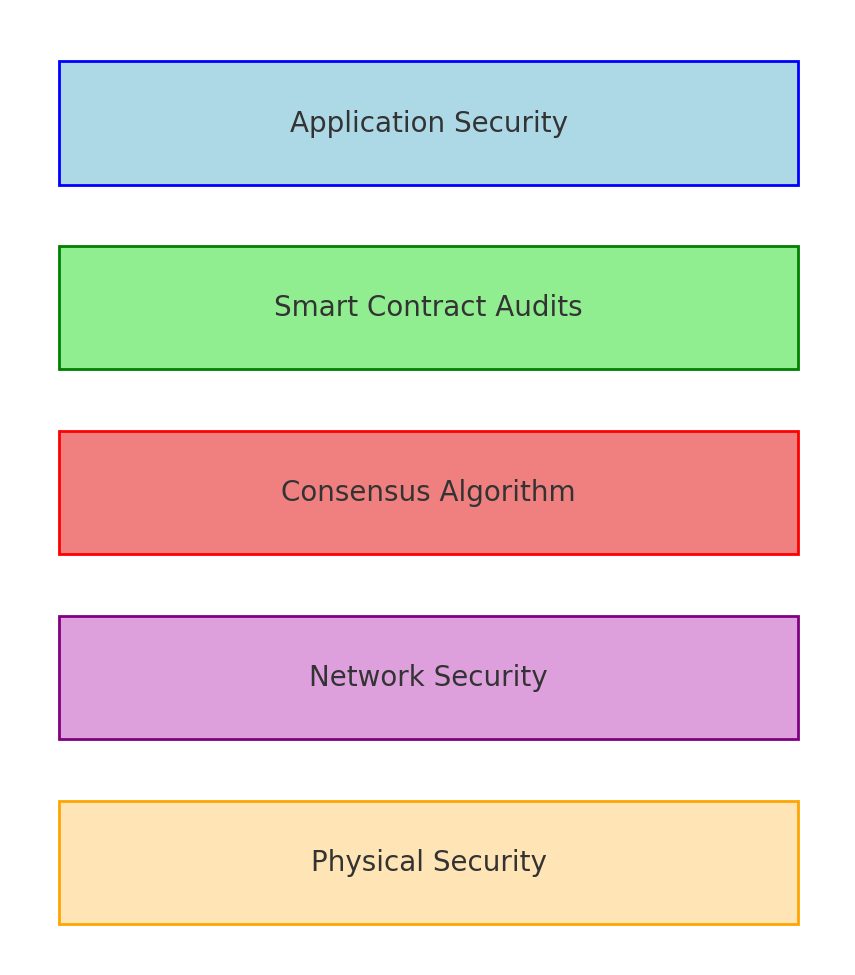
Multi-Layer Security Protocols
Advanced blockchain systems often employ multi-layer security protocols to ensure transaction integrity, user authentication, and data encryption.
Layered Architecture
Some blockchain networks use layered security architectures, often involving an application layer, a consensus layer, and a network layer, each with its own set of security protocols.
Common Threats
While blockchain is celebrated for its robust security features, it is not entirely invulnerable. Various threats and vulnerabilities can compromise the integrity of blockchain networks and the assets they manage. Understanding these common threats is essential for both developers and users to take proactive measures for safeguarding their digital assets. In this section, we explore some of the most common threats facing blockchain today.
51% Attacks
A 51% attack occurs when a single entity gains control of more than half of the network’s hash rate, enabling them to manipulate the blockchain’s transaction history and double-spend coins.
How It Works
Once an attacker gains the majority control, they can exclude or modify the ordering of transactions, allowing for double-spending.
Double Spending
Double spending is an act where a single digital token is spent multiple times, usually as a result of network lag or other vulnerabilities like a 51% attack.
Preventive Measures
Blockchain technology naturally combats double-spending through its consensus algorithms and transaction confirmations.
Phishing Scams
Phishing scams trick users into revealing their private keys or other sensitive information, often through deceptive websites or social engineering tactics.
Types of Phishing
- Email Phishing: Scammers impersonate a trusted entity via email.
- Website Phishing: Clone websites that look identical to legitimate platforms to steal information.
Exchange Vulnerabilities
Security vulnerabilities in cryptocurrency exchanges can lead to massive losses. These platforms can be susceptible to various attacks, including DDoS attacks and wallet thefts.
DDoS Attacks
In a DDoS attack, the attacker floods the exchange with excessive requests, making it unavailable for genuine users.
Wallet Thefts
Attackers may target the hot wallets of an exchange, leading to the loss of funds stored in them.
Advanced Threats
Beyond the common threats that many are aware of, there exists a category of advanced threats that are often less understood but equally perilous. These sophisticated attack vectors primarily target enterprise-level blockchain networks and high-value individual accounts. In this section, we will explore some of these advanced threats that pose a significant risk to blockchain security.
Sybil Attacks
In a Sybil attack, a single adversary controls multiple nodes in a network, primarily to subvert its functionality. These attacks can be particularly harmful to decentralized systems.
How Sybil Attacks Work
The attacker creates a large number of pseudonymous identities and seeks to gain a disproportionately large influence.
Routing Attacks
Routing attacks involve manipulating the network in such a way that all information passing through the network is controlled or observed by the attacker.
Types of Routing Attacks
- Partitioning Attacks: The network is divided into isolated sub-networks.
- Delay Attacks: Transaction data is intentionally delayed.
Eclipse Attacks
An eclipse attack occurs when an attacker isolates a specific node or nodes from the network, feeding them false information and potentially leading to a double-spend or other fraudulent activities.
Mechanism of Eclipse Attacks
The attacker monopolizes all outgoing connections from a victim node, essentially isolating it from the rest of the network.
Timejacking Attacks
In a timejacking attack, the attacker manipulates the timestamps of the network nodes, causing a discrepancy in the time verification process of the blockchain.
Impact of Timejacking
This attack can lead to a variety of adverse effects, including transaction delays and blockchain forks.
- Attacker Alters System Time: The first step in a timejacking attack where the attacker modifies the system time of a targeted node.
- False Timestamps in New Blocks: The altered time is used to generate blocks with false timestamps.
- Network Desynchronization: Nodes in the network start to desynchronize due to the altered timestamps.
- Transaction Verification Issues: Transaction verification becomes problematic as the timestamps do not match, leading to potential double-spending.
- Incorrect Block Addition: Blocks added to the blockchain may be incorrect or malicious due to skewed time verification.
Front-Running Attacks
Front-running occurs when an attacker gains access to pending transactions and sequences their own transactions to gain some form of financial advantage.
Countermeasures
Various blockchain protocols are working on solutions to prevent front-running, such as encrypted transactions and randomized transaction ordering.
Mitigation Strategies
In the ever-evolving landscape of blockchain technology, staying one step ahead of potential threats is crucial. While the risks are real, numerous mitigation strategies can significantly reduce the vulnerability of blockchain networks and secure digital assets. This section will provide an in-depth look at some of these strategies, designed to counter both common and advanced threats.
Multi-Signature Wallets
Multi-signature wallets require more than one signature—or private key—to authorize a blockchain transaction. They are an effective way to add an additional layer of security.
Advantages and Disadvantages
- Advantages: Enhanced security, and reduced risk of unauthorized access.
- Disadvantages: More complicated to set up and manage.
Cold Storage
Cold storage involves keeping a reserve of cryptocurrency offline, making it inaccessible to online hackers.
Types of Cold Storage
- Hardware Wallets
- Paper Wallets
- Air-Gapped (Cold) Computers
Hardware Wallets
Hardware wallets are physical devices that store the user’s private keys offline. They are considered one of the most secure options for storing cryptocurrency.
How to Choose a Hardware Wallet
Factors to consider include the reputation of the manufacturer, ease of use, and the types of cryptocurrencies supported.
| Hardware Wallet | Security Features | Supported Cryptocurrencies | Cost |
|---|---|---|---|
| Safepal | EAL5+ certified Secure Element, PIN protection, 24-word recovery phrase (Small screen and camera for offline transaction authentication) | More than 1,000 | $49.99 |
| Trezor | EAL5+ certified Secure Element, PIN protection, 24-word recovery phrase, Bluetooth connectivity, built-in display | More than 1,800 | $67 (Model One), $213 (Model T) |
| Ledger | EAL5+ certified Secure Element, PIN protection, 24-word recovery phrase, built-in touchscreen | More than 5,500 | $79 (Nano S Plus), $149 (Nano X) |
| Ellipal Titan | Air-gapped design, 24-word recovery phrase | More than 400 | $139 |
| KeepKey | EAL5+ certified Secure Element, PIN protection, 24-word recovery phrase | More than 1,700 | $149 |
Network Monitoring and Anomaly Detection
Constant monitoring of network activity can alert administrators to abnormal patterns, which could indicate a security breach.
Tools and Techniques
- Machine Learning Algorithms
- Real-Time Alert Systems
Smart Contract Audits
For applications relying on smart contracts, regular audits can identify vulnerabilities before they can be exploited.
Importance of Third-Party Audits
Third-party audits offer an unbiased review of the smart contract code, which can be invaluable for identifying overlooked vulnerabilities.
Secure Backup Solutions
Regularly backing up sensitive data and keys can prevent loss from both technical glitches and security breaches.
Best Practices
- Encrypt backups.
- Store backups in multiple secure locations.
Regulatory Landscape
Navigating the complex regulatory environment is another crucial aspect of blockchain security. As governments and international organizations begin to pay closer attention to the rapid growth of blockchain technologies and cryptocurrencies, regulations are evolving to bring more structure and safety to the sector. This section aims to outline the current regulatory landscape, focusing on key legislation, international considerations, and future trends.
Current Laws and Regulations
Various countries have started to frame laws and regulations that govern the usage of blockchain and cryptocurrencies.
Anti-Money Laundering (AML) and Know Your Customer (KYC)
These regulations require identity verification for individuals using cryptocurrency exchanges and are designed to prevent financial crimes.
Securities Regulations
In some jurisdictions, tokens and cryptocurrencies are considered securities and are subject to specific regulations.
International Considerations
Blockchain is a global phenomenon, and its regulatory landscape is not confined to any single jurisdiction.
The Role of International Organizations
Organizations like the United Nations and the International Monetary Fund are increasingly involved in shaping global blockchain regulations.
Cross-Border Regulations
Issues such as cross-border transactions and international trade using cryptocurrencies are still in regulatory grey areas.
The Future of Blockchain Regulations
As the technology matures, it is likely that we will see more refined and comprehensive laws governing its use.
Upcoming Legislation
Several countries are in the process of drafting new laws to govern blockchain technologies, focusing on consumer protection, data privacy, and more.
Regulatory Challenges
The decentralized nature of blockchain presents unique challenges for regulators, including jurisdictional issues and enforcement limitations.
Niche Topics
In addition to the fundamental aspects of blockchain security, there are several niche topics that warrant attention due to their specialized nature and relevance to specific applications or user groups. This section aims to shed light on these less-discussed but highly pertinent areas in blockchain security.
Quantum Computing Threats
The advent of quantum computing poses a potential risk to the cryptographic algorithms that underlie blockchain technology.
Quantum Resistant Algorithms
New cryptographic algorithms are being developed to withstand attacks from quantum computers.
Sidechains and Security
Sidechains allow for more flexible data processing but come with their own set of security concerns.
Pegged Sidechains
These are sidechains whose assets are linked to the main chain, providing an additional layer of security.
Security Token Offerings (STOs)
STOs are considered a more secure alternative to Initial Coin Offerings (ICOs) due to their adherence to legal frameworks.
Regulatory Compliance
STOs are often compliant with securities regulations, offering an added layer of legal security.
Zk-SNARKs and Privacy
Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (zk-SNARKs) are cryptographic methods that allow one party to prove to another that they possess certain information without revealing it.
Applications in Blockchain
Zk-SNARKs are increasingly being used in blockchain for creating privacy-centric solutions.
Decentralized Identity
Blockchain can be used to create decentralized identity systems that are more secure and user-centric than traditional ID systems.
How It Works
Users can have direct control over their personal data, sharing only what is necessary for each interaction.
Real-World Case Studies
Nothing brings the importance of blockchain security into sharper focus than real-world examples. Case studies serve as valuable learning experiences for understanding the vulnerabilities, consequences, and necessary protective measures in the realm of blockchain. This section will delve into notable case studies that offer key insights into various aspects of blockchain security.
The Mt. Gox Meltdown
One of the most infamous events in the history of cryptocurrencies is the collapse of Mt. Gox, a Bitcoin exchange that was hacked in 2014.
What Happened
Hackers exploited a weakness in the exchange’s security protocol, making off with approximately 850,000 Bitcoins.
The DAO Hack
The DAO, a decentralized autonomous organization, was drained of about $50 million in Ethereum due to a vulnerability in its smart contract.
Lessons Learned
The event led to a hard fork in the Ethereum blockchain and a change in the perception of smart contract vulnerabilities.
The Binance Security Breach
In 2019, cryptocurrency exchange Binance suffered a security breach, resulting in a loss of $40 million worth of Bitcoin.
How It Was Mitigated
Binance used its “SAFU” (Secure Asset Fund for Users) to cover the losses, and it also made significant changes to its security protocols.
The Parity Wallet Incident
Parity, an Ethereum wallet, faced an issue where an inexperienced user accidentally froze over 500,000 Ether in multiple accounts.
Impact and Resolution
The incident is still unresolved and has led to ongoing discussions about the ethical considerations of altering blockchain data to rectify such issues.
Supply Chain Security: Maersk and IBM
Maersk, the shipping giant, partnered with IBM to create a blockchain-based supply chain system to enhance transparency and security.
Success Metrics
The partnership led to reduced paperwork, decreased shipping time, and enhanced overall security.
These case studies serve as cautionary tales and learning opportunities for individuals and organizations involved in cryptocurrency trading, smart contracts, and other blockchain-related activities. Each case presents unique challenges and solutions, contributing to our collective understanding of blockchain security.
Securing Your Blockchain Future
As we journey through the multifaceted world of blockchain security, it’s clear that this technology—while revolutionary—is not without its challenges and vulnerabilities. From the basic elements that constitute its secure nature to the real-world incidents that shook the crypto community, every facet offers lessons for enhancing blockchain security. Whether you’re a developer, a trader, or simply a blockchain enthusiast, understanding these intricacies can fortify your interactions within this disruptive technology.
To navigate this complex landscape successfully, it’s essential to stay updated on both regulatory changes and emerging threats. Moreover, adopting proven mitigation strategies can substantially reduce risks and protect your digital assets. As the blockchain ecosystem continues to evolve, the only constant is change. By staying informed and vigilant, you can ensure that you’re not just a part of this exciting future, but you’re also securing it.
Additional Resources
For those eager to delve deeper into the complexities of blockchain security, a wealth of resources is available to satisfy your curiosity and bolster your expertise. Here’s a curated list of books, online courses, and articles to guide your exploration.
Books
- “Mastering Blockchain: Unlocking the Power of Cryptocurrencies, Smart Contracts, and Decentralized Applications” by Imran Bashir
- “Cryptoassets: The Innovative Investor’s Guide to Bitcoin and Beyond” by Chris Burniske and Jack Tatar
Online Courses
- “Blockchain Basics” by Coursera
- “Ethereum and Solidity: The Complete Developer’s Guide” on Udemy
Articles and Papers
- “Blockchain security: What keeps your transaction data safe?” by IBM
- “Anatomy of a Blockchain Attack” published in the Harvard Business Review
Websites and Blogs
- CryptoMindPro’s Comprehensive Guide to Blockchain Technology
- CryptoMindPro on Cryptocurrency Security
Webinars and Podcasts
- “The Security Challenges in Blockchain” by Deloitte Webinar Series
- “Unchained” Podcast focusing on blockchain and cryptocurrency
Forums and Communities
- Reddit’s r/Blockchain
- Stack Exchange for Blockchain
Frequently Asked Questions (FAQs)
Here are some of the most commonly asked questions about blockchain security, along with succinct answers to help you grasp the essentials.
| Question | Answer |
| What is a 51% attack? | A 51% attack occurs when an individual or group controls more than 50% of a blockchain network’s hash rate, enabling them to manipulate the blockchain and double-spend coins. |
| How does a multi-signature wallet enhance security? | A multi-signature wallet requires multiple private keys to authorize a transaction, adding an extra layer of security against unauthorized access. |
| Are smart contracts vulnerable to hacking? | While smart contracts are designed to be secure, vulnerabilities in the contract code can be exploited. Regular smart contract audits can help identify and fix these weaknesses. |
| What are zk-SNARKs? | Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (zk-SNARKs) are cryptographic methods that allow secure, private transactions on blockchain networks. |
| How can I protect my assets from phishing scams? | Be cautious of unsolicited communications asking for personal information and always double-check URLs and email addresses to ensure they’re from a trusted source. |
| What’s the role of regulations in blockchain security? | Regulations like Anti-Money Laundering (AML) and Know Your Customer (KYC) aim to prevent illegal activities and enhance the overall security of cryptocurrency exchanges. |
| Can quantum computing break blockchain? | While not currently a threat, future advancements in quantum computing could potentially crack existing cryptographic algorithms. Research into quantum-resistant algorithms is ongoing. |
| What are the security risks associated with sidechains? | Sidechains allow for more flexible data processing but can be vulnerable to their own set of security risks, such as double-spending and replay attacks. |
| How do hardware wallets work? | Hardware wallets are physical devices that store your private keys offline, providing enhanced security against online hacks. |
| What were the consequences of the Mt. Gox hack? | The Mt. Gox hack led to the loss of 850,000 Bitcoins and exposed severe vulnerabilities in the exchange’s security protocols, eventually leading to its collapse. |


![Comparative Analysis of Consensus Algorithms of Blockchain Technology - Scientific Figure on ResearchGate. Available from: https://www.researchgate.net/figure/Flowchart-of-PoS-algorithm_fig2_348355281 [accessed 4 Oct, 2023]](https://cryptomindpro.com/wp-content/uploads/2023/10/Flowchart-of-PoS-algorithm.png)


